Quantum Computing: Future cryptographic risks
Chinese researchers at Shanghai University successfully cracked RSA encryption using a quantum computer. This breakthrough has significants implications for digital security, with experts raising alarms over the future vulnerability of encrypted data.
The quantum computing experiment, conducted on a D-Wave Advantage quantum computer, marks a historic milestone. The researchers managed to break RSA encryption, a standard widely trusted for securing online communications, emails, and VPNs.
The Challenge of Breaking RSA
RSA encryption relies on the difficulty of factorizing large prime numbers—a task that was, until now, nearly impossible with classical computers. The complexity is so significant that cracking an RSA-encrypted message with traditional methods would take thousands of years. Yet, quantum computing has turned this paradigm upside down.
Quantum Computing to the Rescue
Using a combination of a quantum algorithm and classical methods, the Shanghai team managed to factorize a 50-bit RSA integer. Although 50-bit numbers are relatively small, this breakthrough hints at future capabilities that could jeopardize even the most robust RSA systems in use today.
Quantum Annealing
The experiment utilized a technique called quantum annealing, a method that finds optimal solutions to complex problems faster than classical computers. By harnessing a D-Wave quantum computer with 5,000 qubits, the researchers completed the RSA factorization in just one hour at a cost of $2,000 through cloud computing services.
RSA isn’t the only encryption standard at risk. The Shanghai researchers also targeted AES (Advanced Encryption Standard), another widely-used cryptographic protocol. AES is integral to HTTPS, secure communications, and numerous encrypted platforms that protect data in 2024.
The Looming Threat
With quantum capabilities advancing rapidly, the threat extends to sensitive information safeguarded by RSA-2048, which secures:
- Financial transactions
- Medical records
- Administrative access to servers
- Many other sensitive systems
If RSA-2048, the robust form of RSA used for high-security applications, becomes vulnerable to quantum attacks, the consequences could be catastrophic.
One particularly concerning strategy that quantum advancements enable is “Harvest Now, Decrypt Later.” In this approach, encrypted data is collected today, anticipating future decryption once quantum technology matures. Some governments have allegedly been employing this tactic for years, stockpiling encrypted data that could become accessible once quantum technology advances.
The Global Impact: Urgency of Post-Quantum Cryptography
The urgency to move towards post-quantum cryptography has never been greater. Experts are warning that current encryption standards might not be able to withstand the computational power of future quantum computers. The call for change is immediate:
- Developing new cryptographic standards that can resist quantum attacks
- Implementing post-quantum algorithms for data protection
- Updating systems and protocols to ensure they remain secure in a quantum future
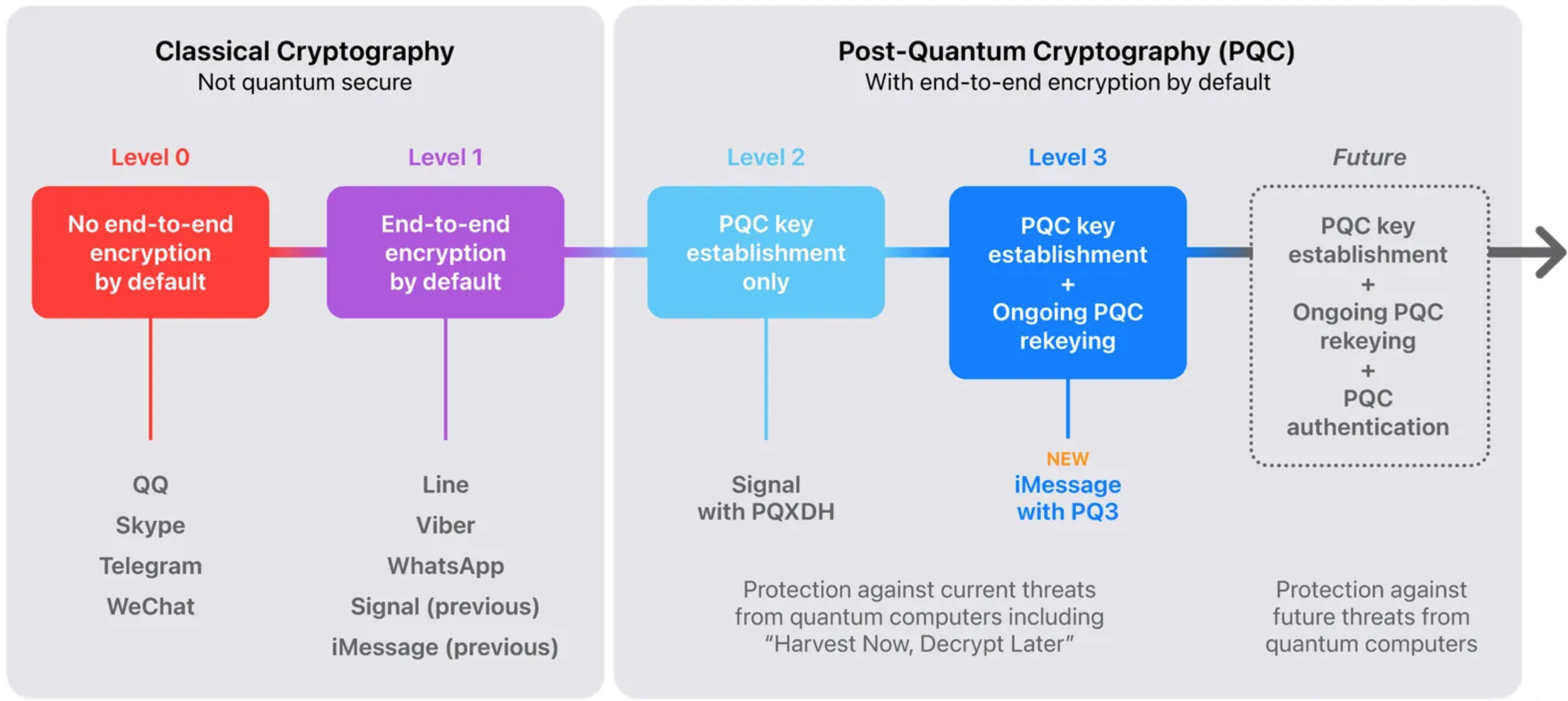
Leading tech companies are already preparing for this seismic shift. For example, Apple has introduced the PQ3 protocol, aiming to future-proof user data against upcoming quantum threats. These steps indicate the beginning of a comprehensive move towards safeguarding information in the post-quantum era.
Conclusion
The recent quantum breakthrough by Chinese researchers is a wake-up call for the entire cybersecurity community. The encryption protocols we rely on today, like RSA and AES, may not be safe tomorrow. The urgency to transition to post-quantum cryptography is clear—this shift is not a matter of if, but when. Those who fail to adapt could face severe consequences, as the digital world moves into an era defined by quantum technology.
Now you know why the security community considers this a historic moment—the end of RSA, as we know it, is comming.
source: CSO